Iran’s State TV Hijacked Mid-Broadcast Amid Geopolitical Tensions; $90M Stolen in Crypto Heist
Iranian State TV Hacked to Broadcast Anti-Government Messages
Iran’s state-run television was hacked on Wednesday night, disrupting regular programming to broadcast videos urging citizens to take to the streets in protest against the government, according to multiple reports.
The identity of the hackers remains unknown, though Iranian authorities have suggested Israeli involvement, as reported by Iran International.
“If you notice disruptions or unusual messages on various TV channels, it is due to enemy interference with satellite signals,” the broadcaster stated.
This attack on state TV is the latest in a series of cyber incidents inside Iran believed to be linked to Israeli-affiliated actors. It comes alongside recent breaches at Bank Sepah and Nobitex — Iran’s largest cryptocurrency exchange.
The Nobitex hack alone resulted in the theft of over $90 million, marking a significant escalation in the long-standing cyber conflict between Iran and Israel.
“Iranian groups have explored the use of virtual assets not only as a means to bypass financial restrictions, but also as strategic tools to advance broader geopolitical goals — including the development of sophisticated weapons systems,” said TRM Labs. “This latest incident underscores how cryptocurrency exchanges, once seen as peripheral to global conflicts, are now emerging as high-value targets for geopolitical players.”
This development comes on the heels of Israeli officials revealing that Iran has been hacking into private security cameras in Israel to collect real-time intelligence — a tactic reminiscent of Russia’s strategy following its 2022 invasion of Ukraine.
“In the past two or three days, we’ve seen Iranian efforts to tap into surveillance cameras to determine missile impact locations and improve targeting accuracy,” said Refael Franco, former deputy director general of Israel’s National Cyber Directorate.
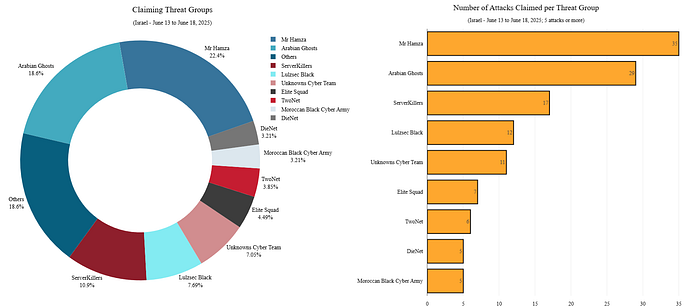
Groups claiming DDoS attacks targeting Israel between June 13 and June 18, 2025 | Source: Radware
Cybersecurity firm Radware reports that nearly 40% of all hacktivist-led DDoS attacks since the start of the current conflict have targeted Israel. On June 17, the hacktivist group DieNet issued a warning, threatening cyberattacks against the United States if it becomes involved in the confrontation with Iran.
This threat has been echoed and amplified by other groups, including Arabian Ghosts, Sylhet Gang, and Team Fearless — indicating the emergence of a potential cyber alliance as the physical conflict escalates.
“Organizations must exercise heightened vigilance. The warning signs are unmistakable,” said Pascal Geenens, Director of Threat Intelligence at Radware. “Critical infrastructure, supply chains, and global enterprises are at risk of becoming unintended casualties if the cyber conflict intensifies.”
“The Israel-Iran conflict of 2025 is a vivid example of hybrid warfare, where digital attacks and information campaigns are as integral to the battlefield as traditional military force.”
In a two-part analysis, cybersecurity firm CloudSEK reported that over 35 pro-Iranian hacktivist groups have launched coordinated cyberattacks targeting Israeli infrastructure — significantly outnumbering the fewer than half a dozen pro-Israeli groups engaged in similar activity.
“The majority of these attacks have involved DDoS campaigns, website defacements, and alleged data breaches, aimed at government platforms, military systems, and critical infrastructure,” said security researcher Pagilla Manohar Reddy.
Notably, Reddy emphasized that many of these incidents follow a familiar pattern of exaggeration and disinformation. “Hacktivist groups often claim responsibility for unrelated service disruptions, recycle old data leaks, and inflate the scale of their attacks to attract media attention — prioritizing visibility over real operational impact,” he said.

Comments
Post a Comment